IMPORTANT: Disable GRE keepalive on the Tunnel (they will be sent without encryption and dropped on the other end. As a consequence the tunnel will go down). IPSec has it's own keepalive.
Parameters to consider/agree upon
Phase 1 IKE/ISAKMP
- Authentication : RSA
- Mode : Main
- Key Exchange Encryption: AES-25
- Hash: SHA1
- Diffie-Hellman Group: 2
- Lifetime: 86400 seconds
Phase 2 IPSec
- Encryption: AES-128
- Hash: SHA1
- PFS Diffie-Hellman group: 2
- Lifetime: 36000
Phase 1 config
crypto keyring kr-acme
rsa-pubkey address
key-string
HEXHEXHEX
quit
!
crypto isakmp policy 10
encr aes 256
hash sha256
group 2
!
crypto isakmp profile isa-acme
keyring kr-acme
match identity address 23.0.0.3 255.255.255.255
Phase 2 config
crypto ipsec transform-set ts-acme esp-aes 256 esp-sha-hmac
mode tunnel
!
!
crypto ipsec profile ipsec-acme
set security-association replay disable
set transform-set ts-acme
set isakmp-profile isa-acme
Phase 1 Troubleshooting
#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
12.0.0.1 23.0.0.3 MM_KEY_EXCH 1019 ACTIVE
23.0.0.3 12.0.0.1 MM_KEY_EXCH 1020 ACTIVE
#show crypto isakmp diagnose error
...
Error(103): Failed to find public key. (address is missing in keyring)
Error(2): Failed to verify signature. (signature is corrupt)
Phase 2 Troubleshooting
R1#sh crypto ipsec transform-set
...
Transform set ts-acme: { esp-256-aes esp-sha-hmac }
will negotiate = { Tunnel, },
R1#sh crypto ipsec profile
...
IPSEC profile ipsec-acme
ISAKMP Profile: isa-acme
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Mixed-mode : Disabled
Transform sets={
ts-acme: { esp-256-aes esp-sha-hmac } ,
}
Antireplay window disabled
R1#sh crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 12.0.0.1
protected vrf: (none)
local ident (addr/mask/prot/port): (12.0.0.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (23.0.0.3/255.255.255.255/47/0)
current_peer 23.0.0.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 12.0.0.1, remote crypto endpt.: 23.0.0.3
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0xC288357(203981655)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x89A123AF(2309039023)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, sibling_flags 80000040, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4235169/3427)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xC288357(203981655)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80000040, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4235169/3427)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
R1# show crypto session detail
Crypto session current status
Code: C - IKE Configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal, T - cTCP encapsulation
X - IKE Extended Authentication, F - IKE Fragmentation
R - IKE Auto Reconnect, U - IKE Dynamic Route Update
Interface: Tunnel0
Profile: isa-acme
Uptime: 00:05:51
Session status: UP-ACTIVE
Peer: 23.0.0.3 port 500 fvrf: (none) ivrf: (none)
Phase1_id: 23.0.0.3
Desc: (none)
Session ID: 0
IKEv1 SA: local 12.0.0.1/500 remote 23.0.0.3/500 Active
Capabilities:(none) connid:1021 lifetime:23:54:08
IPSEC FLOW: permit 47 host 12.0.0.1 host 23.0.0.3
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 5 drop 0 life (KB/Sec) 4235169/3248
Outbound: #pkts enc'ed 5 drop 0 life (KB/Sec) 4235169/3248
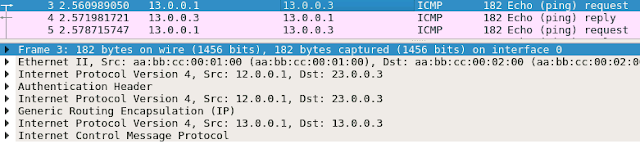
Wireshark
(AH instead of ESP is used as transform-set so no encryption of the payload)
ping interface 12.0.0.1->23.0.0.3 no IPSec
Ping tunnel 13.0.0.1->13.0.0.3 no IPSec
Ping tunnel IPs 13.0.0.1->13.0.0.3 IPSec mode tunnel
Ping tunnel IPSec mode transport
Remarks
Both modes , tunnel and transport, encrypt full GRE packet.
mode Tunnel = new IP header is created
mode Transport = existing IP header is copied to front



No comments:
Post a Comment