Friday, October 19, 2018
Friday, August 24, 2018
VPN (GRE+IPSec)
Cisco VPN (GRE+IPSec)
IMPORTANT: Disable GRE keepalive on the Tunnel (they will be sent without encryption and dropped on the other end. As a consequence the tunnel will go down). IPSec has it's own keepalive.
Parameters to consider/agree upon
Phase 1 IKE/ISAKMP
- Authentication : RSA
- Mode : Main
- Key Exchange Encryption: AES-25
- Hash: SHA1
- Diffie-Hellman Group: 2
- Lifetime: 86400 seconds
Phase 2 IPSec
- Encryption: AES-128
- Hash: SHA1
- PFS Diffie-Hellman group: 2
- Lifetime: 36000
Phase 1 config
crypto keyring kr-acme
rsa-pubkey address
key-string
HEXHEXHEX
quit
!
crypto isakmp policy 10
encr aes 256
hash sha256
group 2
!
crypto isakmp profile isa-acme
keyring kr-acme
match identity address 23.0.0.3 255.255.255.255
Phase 2 config
crypto ipsec transform-set ts-acme esp-aes 256 esp-sha-hmac
mode tunnel
!
!
crypto ipsec profile ipsec-acme
set security-association replay disable
set transform-set ts-acme
set isakmp-profile isa-acme
Phase 1 Troubleshooting
#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
12.0.0.1 23.0.0.3 MM_KEY_EXCH 1019 ACTIVE
23.0.0.3 12.0.0.1 MM_KEY_EXCH 1020 ACTIVE
#show crypto isakmp diagnose error
...
Error(103): Failed to find public key. (address is missing in keyring)
Error(2): Failed to verify signature. (signature is corrupt)
Phase 2 Troubleshooting
R1#sh crypto ipsec transform-set
...
Transform set ts-acme: { esp-256-aes esp-sha-hmac }
will negotiate = { Tunnel, },
R1#sh crypto ipsec profile
...
IPSEC profile ipsec-acme
ISAKMP Profile: isa-acme
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Mixed-mode : Disabled
Transform sets={
ts-acme: { esp-256-aes esp-sha-hmac } ,
}
Antireplay window disabled
R1#sh crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 12.0.0.1
protected vrf: (none)
local ident (addr/mask/prot/port): (12.0.0.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (23.0.0.3/255.255.255.255/47/0)
current_peer 23.0.0.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 12.0.0.1, remote crypto endpt.: 23.0.0.3
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0xC288357(203981655)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x89A123AF(2309039023)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, sibling_flags 80000040, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4235169/3427)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xC288357(203981655)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80000040, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4235169/3427)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
R1# show crypto session detail
Crypto session current status
Code: C - IKE Configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal, T - cTCP encapsulation
X - IKE Extended Authentication, F - IKE Fragmentation
R - IKE Auto Reconnect, U - IKE Dynamic Route Update
Interface: Tunnel0
Profile: isa-acme
Uptime: 00:05:51
Session status: UP-ACTIVE
Peer: 23.0.0.3 port 500 fvrf: (none) ivrf: (none)
Phase1_id: 23.0.0.3
Desc: (none)
Session ID: 0
IKEv1 SA: local 12.0.0.1/500 remote 23.0.0.3/500 Active
Capabilities:(none) connid:1021 lifetime:23:54:08
IPSEC FLOW: permit 47 host 12.0.0.1 host 23.0.0.3
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 5 drop 0 life (KB/Sec) 4235169/3248
Outbound: #pkts enc'ed 5 drop 0 life (KB/Sec) 4235169/3248
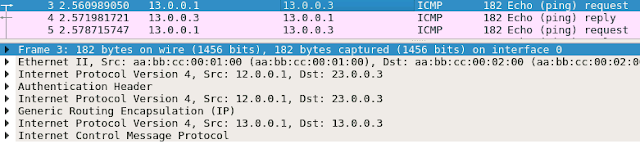
Wireshark
(AH instead of ESP is used as transform-set so no encryption of the payload)
ping interface 12.0.0.1->23.0.0.3 no IPSec
Ping tunnel 13.0.0.1->13.0.0.3 no IPSec
IMPORTANT: Disable GRE keepalive on the Tunnel (they will be sent without encryption and dropped on the other end. As a consequence the tunnel will go down). IPSec has it's own keepalive.
Parameters to consider/agree upon
Phase 1 IKE/ISAKMP
- Authentication : RSA
- Mode : Main
- Key Exchange Encryption: AES-25
- Hash: SHA1
- Diffie-Hellman Group: 2
- Lifetime: 86400 seconds
Phase 2 IPSec
- Encryption: AES-128
- Hash: SHA1
- PFS Diffie-Hellman group: 2
- Lifetime: 36000
Phase 1 config
crypto keyring kr-acme
rsa-pubkey address
key-string
HEXHEXHEX
quit
!
crypto isakmp policy 10
encr aes 256
hash sha256
group 2
!
crypto isakmp profile isa-acme
keyring kr-acme
match identity address 23.0.0.3 255.255.255.255
Phase 2 config
crypto ipsec transform-set ts-acme esp-aes 256 esp-sha-hmac
mode tunnel
!
!
crypto ipsec profile ipsec-acme
set security-association replay disable
set transform-set ts-acme
set isakmp-profile isa-acme
Phase 1 Troubleshooting
#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
12.0.0.1 23.0.0.3 MM_KEY_EXCH 1019 ACTIVE
23.0.0.3 12.0.0.1 MM_KEY_EXCH 1020 ACTIVE
#show crypto isakmp diagnose error
...
Error(103): Failed to find public key. (address is missing in keyring)
Error(2): Failed to verify signature. (signature is corrupt)
Phase 2 Troubleshooting
R1#sh crypto ipsec transform-set
...
Transform set ts-acme: { esp-256-aes esp-sha-hmac }
will negotiate = { Tunnel, },
R1#sh crypto ipsec profile
...
IPSEC profile ipsec-acme
ISAKMP Profile: isa-acme
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Mixed-mode : Disabled
Transform sets={
ts-acme: { esp-256-aes esp-sha-hmac } ,
}
Antireplay window disabled
R1#sh crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 12.0.0.1
protected vrf: (none)
local ident (addr/mask/prot/port): (12.0.0.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (23.0.0.3/255.255.255.255/47/0)
current_peer 23.0.0.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 12.0.0.1, remote crypto endpt.: 23.0.0.3
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0xC288357(203981655)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x89A123AF(2309039023)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, sibling_flags 80000040, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4235169/3427)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xC288357(203981655)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80000040, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4235169/3427)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
R1# show crypto session detail
Crypto session current status
Code: C - IKE Configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal, T - cTCP encapsulation
X - IKE Extended Authentication, F - IKE Fragmentation
R - IKE Auto Reconnect, U - IKE Dynamic Route Update
Interface: Tunnel0
Profile: isa-acme
Uptime: 00:05:51
Session status: UP-ACTIVE
Peer: 23.0.0.3 port 500 fvrf: (none) ivrf: (none)
Phase1_id: 23.0.0.3
Desc: (none)
Session ID: 0
IKEv1 SA: local 12.0.0.1/500 remote 23.0.0.3/500 Active
Capabilities:(none) connid:1021 lifetime:23:54:08
IPSEC FLOW: permit 47 host 12.0.0.1 host 23.0.0.3
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 5 drop 0 life (KB/Sec) 4235169/3248
Outbound: #pkts enc'ed 5 drop 0 life (KB/Sec) 4235169/3248
Wireshark
(AH instead of ESP is used as transform-set so no encryption of the payload)
ping interface 12.0.0.1->23.0.0.3 no IPSec
Ping tunnel 13.0.0.1->13.0.0.3 no IPSec
Ping tunnel IPs 13.0.0.1->13.0.0.3 IPSec mode tunnel
Ping tunnel IPSec mode transport
Remarks
Both modes , tunnel and transport, encrypt full GRE packet.
mode Tunnel = new IP header is created
mode Transport = existing IP header is copied to front
Monday, April 30, 2018
Substratum Node on Linux (Ubuntu Server 16.x)
sudo apt-get install ssh openssh-server gcc make pkg-config git
Docker
https://docs.docker.com/install/linux/docker-ce/ubuntu
systemctl start docker
Thursday, April 12, 2018
EVE-NG Troubleshooting
Router doesn't boot
*First try to simply "wipe" the router*
*If the wipe doesn't help do the following*
When the icon goes immediately from blue to grey, you can
Router doesn't boot
*First try to simply "wipe" the router*
*If the wipe doesn't help do the following*
When the icon goes immediately from blue to grey, you can
1)
check if the router is not already running by doing
ps -ef | grep "D <ID of the router>" (you can find the ID of the router by right-clicking on the icon in the GUI
If there are running processes first try to kill it nicely via
kill -15 <ID>
If still running
kill <ID>
If still running
kill -9 <ID>
2)
Read the file /opt/unetlab/data/Logs/unl_wrapper.txt
Go to the directory of the router
Execute the command manually (without the redirect)
This will start a child process
Execute the child command manually and look for errors
Example:
cat /opt/unetlab/data/Logs/unl_wrapper.txt
Read the file /opt/unetlab/data/Logs/unl_wrapper.txt
Go to the directory of the router
Execute the command manually (without the redirect)
This will start a child process
Execute the child command manually and look for errors
Example:
cat /opt/unetlab/data/Logs/unl_wrapper.txt
check the last entries and do the same manually
cd /opt/unetlab/tmp/0/c1c2b011-55e4-4279-b489-0cb8684710bb/5
/opt/unetlab/wrappers/qemu_wrapper -C 49787 -T 0 -D 5 -t "CSR2" -F /opt/qemu-2.2.0/bin/qemu-system-x86_64 -d 0 -- -nographic -device e1000,netdev=net0,mac=50:00:00:05:00:00 -netdev tap,id=net0,ifname=vunl1_0_5_0,script=no -device e1000,netdev=net1,mac=50:00:00:05:00:01 -netdev tap,id=net1,ifname=vunl1_0_5_1,script=no -device e1000,netdev=net2,mac=50:00:00:05:00:02 -netdev tap,id=net2,ifname=vunl1_0_5_2,script=no -device e1000,netdev=net3,mac=50:00:00:05:00:03 -netdev tap,id=net3,ifname=vunl1_0_5_3,script=no -smp 1 -m 3072 -name CSR2 -uuid a2c2cd71-1673-48d0-8907-a135ad73af83 -hda hda.qcow2 -machine type=pc-1.0,accel=kvm -serial mon:stdio -nographic -nodefconfig -nodefaults -rtc base=utc
TAG=T0D5- /opt/qemu-2.2.0/bin/qemu-system-x86_64 -nographic -device e1000,netdev=net0,mac=50:00:00:05:00:00 -netdev tap,id=net0,ifname=vunl1_0_5_0,script=no -device e1000,netdev=net1,mac=50:00:00:05:00:01 -netdev tap,id=net1,ifname=vunl1_0_5_1,script=no -device e1000,netdev=net2,mac=50:00:00:05:00:02 -netdev tap,id=net2,ifname=vunl1_0_5_2,script=no -device e1000,netdev=net3,mac=50:00:00:05:00:03 -netdev tap,id=net3,ifname=vunl1_0_5_3,script=no -smp 1 -m 3072 -name CSR2 -uuid a2c2cd71-1673-48d0-8907-a135ad73af83 -hda hda.qcow2 -machine type=pc-1.0,accel=kvm -serial mon:stdio -nographic -nodefconfig -nodefaults -rtc base=utc
cd /opt/unetlab/tmp/0/c1c2b011-55e4-4279-b489-0cb8684710bb/5
/opt/unetlab/wrappers/qemu_wrapper -C 49787 -T 0 -D 5 -t "CSR2" -F /opt/qemu-2.2.0/bin/qemu-system-x86_64 -d 0 -- -nographic -device e1000,netdev=net0,mac=50:00:00:05:00:00 -netdev tap,id=net0,ifname=vunl1_0_5_0,script=no -device e1000,netdev=net1,mac=50:00:00:05:00:01 -netdev tap,id=net1,ifname=vunl1_0_5_1,script=no -device e1000,netdev=net2,mac=50:00:00:05:00:02 -netdev tap,id=net2,ifname=vunl1_0_5_2,script=no -device e1000,netdev=net3,mac=50:00:00:05:00:03 -netdev tap,id=net3,ifname=vunl1_0_5_3,script=no -smp 1 -m 3072 -name CSR2 -uuid a2c2cd71-1673-48d0-8907-a135ad73af83 -hda hda.qcow2 -machine type=pc-1.0,accel=kvm -serial mon:stdio -nographic -nodefconfig -nodefaults -rtc base=utc
TAG=T0D5- /opt/qemu-2.2.0/bin/qemu-system-x86_64 -nographic -device e1000,netdev=net0,mac=50:00:00:05:00:00 -netdev tap,id=net0,ifname=vunl1_0_5_0,script=no -device e1000,netdev=net1,mac=50:00:00:05:00:01 -netdev tap,id=net1,ifname=vunl1_0_5_1,script=no -device e1000,netdev=net2,mac=50:00:00:05:00:02 -netdev tap,id=net2,ifname=vunl1_0_5_2,script=no -device e1000,netdev=net3,mac=50:00:00:05:00:03 -netdev tap,id=net3,ifname=vunl1_0_5_3,script=no -smp 1 -m 3072 -name CSR2 -uuid a2c2cd71-1673-48d0-8907-a135ad73af83 -hda hda.qcow2 -machine type=pc-1.0,accel=kvm -serial mon:stdio -nographic -nodefconfig -nodefaults -rtc base=utc
Try to see what error message you get.
EVE-NG Troubleshooting
Packets don't show up on the other side of the link
To check the underlying bridge (each link between routers is a hidden bridge), connect to the console of eve (ssh, ...)
*new format as of 4.x*
For example, bridge vnet00100000009 connects
RouterID can be found by right-clicking on the router (shown between brackets), interfaceID is logical (gi0/0 is 0, gi0/1 is 1, etc).
For example, bridge vnet2_0_1 connects router1-interface0 with router4-interface0
More details
root@eve-ng:~# brctl showstp vnet2_0_1
vnet2_0_1
bridge id 8000.2227c4356e60
designated root 8000.2227c4356e60
root port 0 path cost 0
max age 20.00 bridge max age 20.00
hello time 2.00 bridge hello time 2.00
forward delay 15.00 bridge forward delay 15.00
ageing time 0.00
hello timer 0.00 tcn timer 0.00
topology change timer 0.00 gc timer 0.12
flags
vunl2_0_1_0 (1)
port id 8001 state forwarding
designated root 8000.2227c4356e60 path cost 100
designated bridge 8000.2227c4356e60 message age timer 0.00
designated port 8001 forward delay timer 0.00
designated cost 0 hold timer 0.00
flags
vunl2_0_4_0 (2)
port id 8002 state forwarding
designated root 8000.2227c4356e60 path cost 100
designated bridge 8000.2227c4356e60 message age timer 0.00
designated port 8002 forward delay timer 0.00
designated cost 0 hold timer 0.00
flags
If they are not in forwarding then communication will not work. This bridge should disappear when the link is down (neither side has a running router) in the GUI of eve-ng. If it remains try to delete it manually:
brctl delif vnet2_0_1 vunl2_0_1_0
brctl delif vnet2_0_1 vunl2_0_4_0
brctl delbr vnet2_0_1
If the last command doesn't work.Then delete it on a linux level:
root@eve-ng:~# brctl delbr vnet2_0_1
bridge vnet2_0_4 is still up; can't delete it
root@eve-ng:~# ip link del vnet2_0_1
To check on a linux level the status of the interfaces:
ip link | grep vnet
ip link show vunl2_0_4_0
or
dmesg
If the link is down you can do:
ip link set vunl2_0_4_0 up
Packets don't show up on the other side of the link
To check the underlying bridge (each link between routers is a hidden bridge), connect to the console of eve (ssh, ...)
*new format as of 4.x*
root@eve-ng:~# brctl show
bridge name bridge id STP enabled interfaces
docker0 8000.0242133159f4 no screen_46667
screen_47937
nat0 8000.3e0e9e87189a no vun001000004205
vun001000004700
pnet0 8000.0050568e69e1 no eth0
vun001000000700
vun003000b00101
pnet1 8000.0050568eb031 no eth1
pnet2 8000.000000000000 no
pnet3 8000.000000000000 no
pnet4 8000.000000000000 no
pnet5 8000.000000000000 no
pnet6 8000.000000000000 no
pnet7 8000.000000000000 no
pnet8 8000.000000000000 no
pnet9 8000.000000000000 no
vnet00100000004 8000.eac8a9fa3c1a no vun001000004301
vnet00100000008 8000.ba8ea28f5616 no vun001000000a00
vun001000002103
vnet00100000009 8000.76a0d8456b74 no vun001000002400
vun001000002c30
vnet0010000000a 8000.8e69eca20eb5 no vun001000001e00
vun001000004201
vnet0010000000b 8000.8aa0b055cd94 no vun001000004402
vnet00x000000xx are the bridges.
vun00x00000yyzz are the interfaces in your lab.
x = user POD-ID
yy = Router ID in hex-> can be found by right-clicking on the router (shown between brackets) and converting it to hex.
interfaceID is logical (gi0/0 is 0, gi0/1 is 1, etc).
For example, bridge vnet00100000009 connects
vun001000002400 = pod1-router36(hex24)-interface0
with
vun001000002c30 = pod1-router44(hex2c)-interface3
More details
root@eve-ng:~# brctl showstp vnet00100000009
root@eve-ng:~# brctl showstp vnet00100000009
vnet00100000009
bridge id 8000.76a0d8456b74
designated root 8000.76a0d8456b74
root port 0 path cost 0
max age 20.00 bridge max age 20.00
hello time 2.00 bridge hello time 2.00
forward delay 15.00 bridge forward delay 15.00
ageing time 0.00
hello timer 0.00 tcn timer 0.00
topology change timer 0.00 gc timer 0.00
flags
vun001000002400 (2)
port id 8002 state forwarding
designated root 8000.76a0d8456b74 path cost 100
designated bridge 8000.76a0d8456b74 message age timer 0.00
designated port 8002 forward delay timer 0.00
designated cost 0 hold timer 0.00
flags
vun001000002c30 (1)
port id 8001 state forwarding
designated root 8000.76a0d8456b74 path cost 100
designated bridge 8000.76a0d8456b74 message age timer 0.00
designated port 8001 forward delay timer 0.00
designated cost 0 hold timer 0.00
flags
If they are not in forwarding then communication will not work. This bridge should disappear when the link is down (neither side has a running router) in the GUI of eve-ng. If it remains try to delete it manually:
brctl delif vnet00100000009 vun001000002400
brctl delif vnet00100000009 vun001000002c30
brctl delbr vnet00100000009
If the last command doesn't work.Then delete it on a linux level:
root@eve-ng:~# brctl delbr vnet00100000009
bridge vnet00100000009 is still up; can't delete it
root@eve-ng:~# ip link del vnet00100000009
To check on a linux level the status of the bridges &interfaces:
ip link
ip link show vun001000002c30
or
dmesg
If the link is down you can do:
ip link set vun001000002c30 up
brctl delif vnet00100000009 vun001000002400
brctl delif vnet00100000009 vun001000002c30
brctl delbr vnet00100000009
If the last command doesn't work.Then delete it on a linux level:
root@eve-ng:~# brctl delbr vnet00100000009
bridge vnet00100000009 is still up; can't delete it
root@eve-ng:~# ip link del vnet00100000009
To check on a linux level the status of the bridges &interfaces:
ip link
ip link show vun001000002c30
or
dmesg
If the link is down you can do:
ip link set vun001000002c30 up
*old format before 4.x*
root@eve-ng:~# brctl showvnetx_x_x are the bridges. vunlx_x_x_x are the interfaces in your lab. Second last number is the routerID, last number is the interfaceID.
bridge name bridge id STP enabled interfaces
docker0 8000.02426b37243d no screen_0
veth9385b06
nat0 8000.000000000000 no
pnet1 8000.000000000000 no
pnet2 8000.000000000000 no
pnet3 8000.000000000000 no
pnet4 8000.000000000000 no
pnet5 8000.000000000000 no
pnet6 8000.000000000000 no
pnet7 8000.000000000000 no
pnet8 8000.000000000000 no
pnet9 8000.000000000000 no
vnet1_0_18 8000.1e2c061e0be3 no vunl1_0_13_1
vnet1_0_20 8000.ca655da5c77f no vunl1_0_13_0
vnet2_0_1 8000.2227c4356e60 no vunl2_0_1_0
vunl2_0_4_0
vnet2_0_2 8000.1e7262aa3853 no vunl2_0_1_1
vunl2_0_3_0
vnet2_0_3 8000.62a793b91f19 no vunl2_0_1_2
vunl2_0_2_2
vnet2_0_4 8000.76c00a9115ff no vunl2_0_1_3
vnet2_0_5 8000.bac02a706e2c no vunl2_0_1_4
RouterID can be found by right-clicking on the router (shown between brackets), interfaceID is logical (gi0/0 is 0, gi0/1 is 1, etc).
For example, bridge vnet2_0_1 connects router1-interface0 with router4-interface0
More details
root@eve-ng:~# brctl showstp vnet2_0_1
vnet2_0_1
bridge id 8000.2227c4356e60
designated root 8000.2227c4356e60
root port 0 path cost 0
max age 20.00 bridge max age 20.00
hello time 2.00 bridge hello time 2.00
forward delay 15.00 bridge forward delay 15.00
ageing time 0.00
hello timer 0.00 tcn timer 0.00
topology change timer 0.00 gc timer 0.12
flags
vunl2_0_1_0 (1)
port id 8001 state forwarding
designated root 8000.2227c4356e60 path cost 100
designated bridge 8000.2227c4356e60 message age timer 0.00
designated port 8001 forward delay timer 0.00
designated cost 0 hold timer 0.00
flags
vunl2_0_4_0 (2)
port id 8002 state forwarding
designated root 8000.2227c4356e60 path cost 100
designated bridge 8000.2227c4356e60 message age timer 0.00
designated port 8002 forward delay timer 0.00
designated cost 0 hold timer 0.00
flags
If they are not in forwarding then communication will not work. This bridge should disappear when the link is down (neither side has a running router) in the GUI of eve-ng. If it remains try to delete it manually:
brctl delif vnet2_0_1 vunl2_0_1_0
brctl delif vnet2_0_1 vunl2_0_4_0
brctl delbr vnet2_0_1
If the last command doesn't work.Then delete it on a linux level:
root@eve-ng:~# brctl delbr vnet2_0_1
bridge vnet2_0_4 is still up; can't delete it
root@eve-ng:~# ip link del vnet2_0_1
To check on a linux level the status of the interfaces:
ip link | grep vnet
ip link show vunl2_0_4_0
or
dmesg
If the link is down you can do:
ip link set vunl2_0_4_0 up
Subscribe to:
Comments (Atom)
YAML Files for ESP32
Gree Versati III https://gist.github.com/slanckma/3bad4ff49545488a3719766bdf0cdc76 TUF-2000M Water flow sensor https://gist.github.com/slan...
-
/var/log/syslog shows: Jun 18 11:21:18 labusraeveng01 iol_wrapper[105334]: 18/5 15:21:18.639 ERR#011Error while connecting local AF_UNIX: ...
-
install openwrt on e4200v2 Open ssh and http on the WAN (disable firewall) Via GUI of openwrt (LuCi) install tc-full and kmod-netem Injec...
-
zerotouch cancel -> only for current uptime (reload will start ZTP again) zerotouch disable -> forever to reenable zerotouch do: ...